Security Onion on X: "The analyst desktop environment includes: #Chromium #NetworkMiner #wireshark and many other analysis tools! https://t.co/gM3znAuuxl" / X
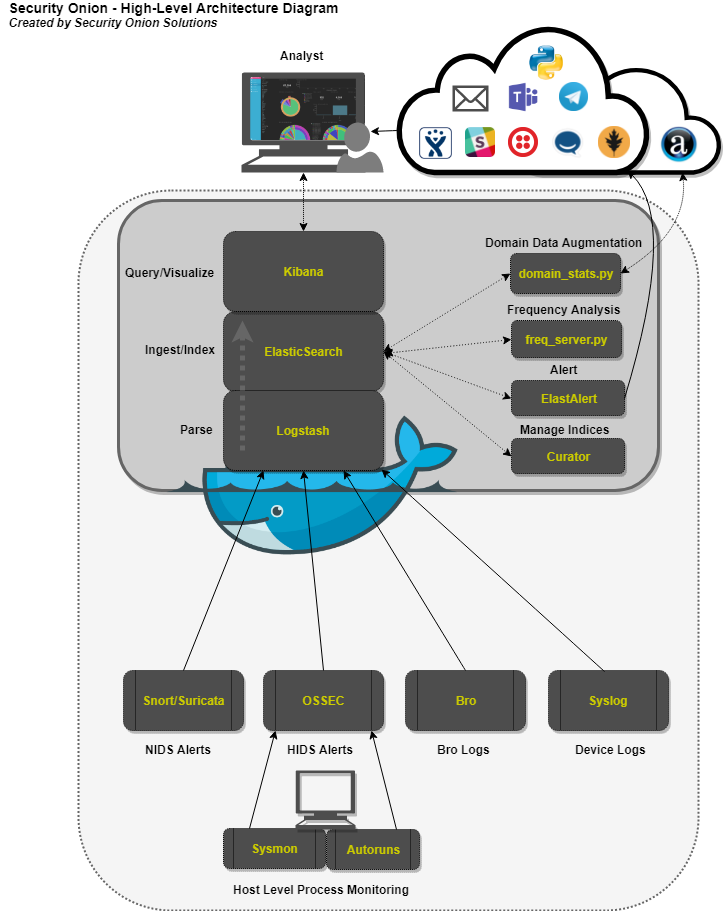
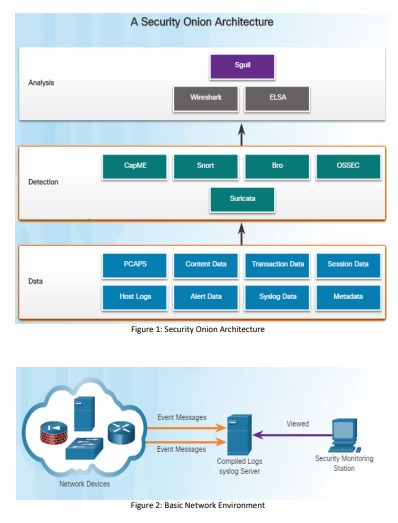
Experimental setup for Security Onion (SecOn) deployment for the SIEM... | Download Scientific Diagram

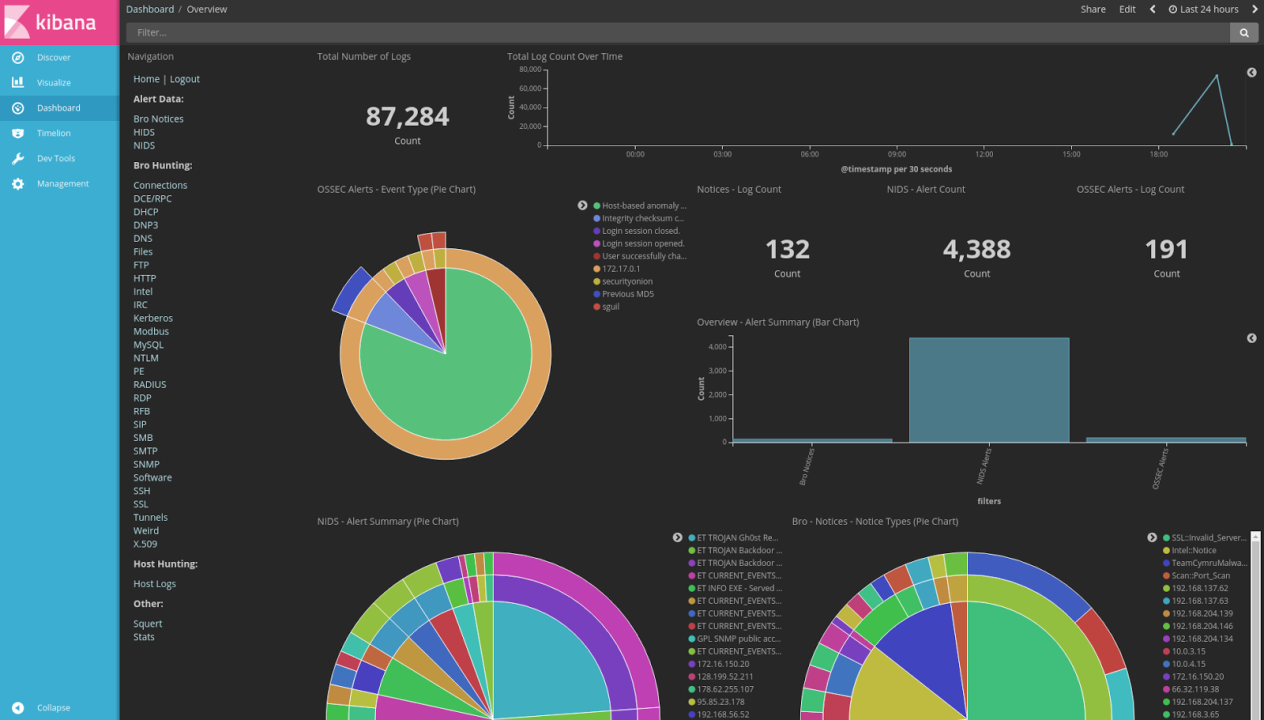
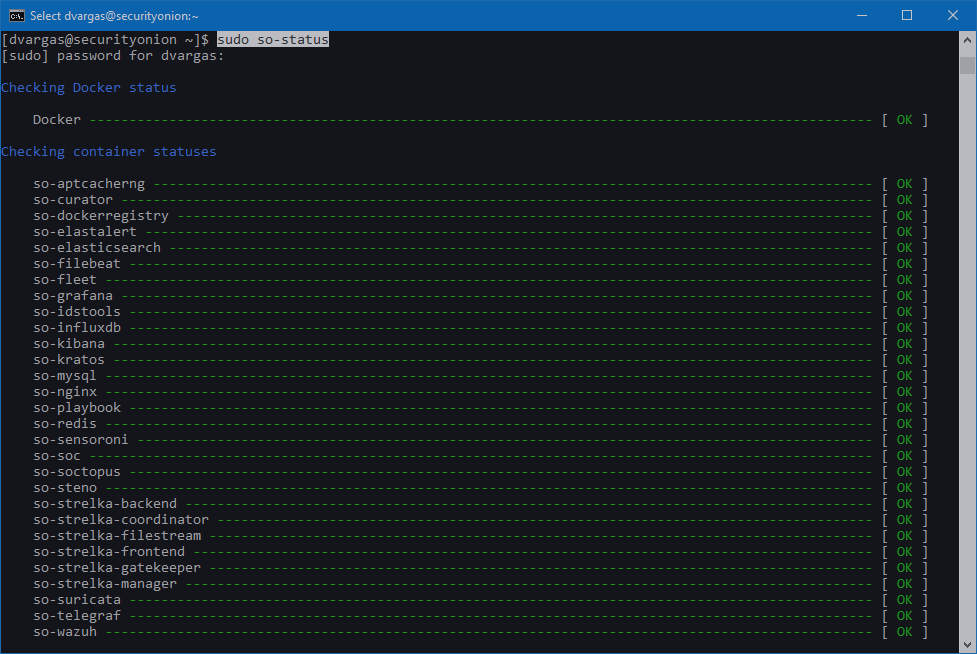
Simple Network Security Monitoring with Security Onion & NetWitness Investigator – CYBER ARMS – Computer Security

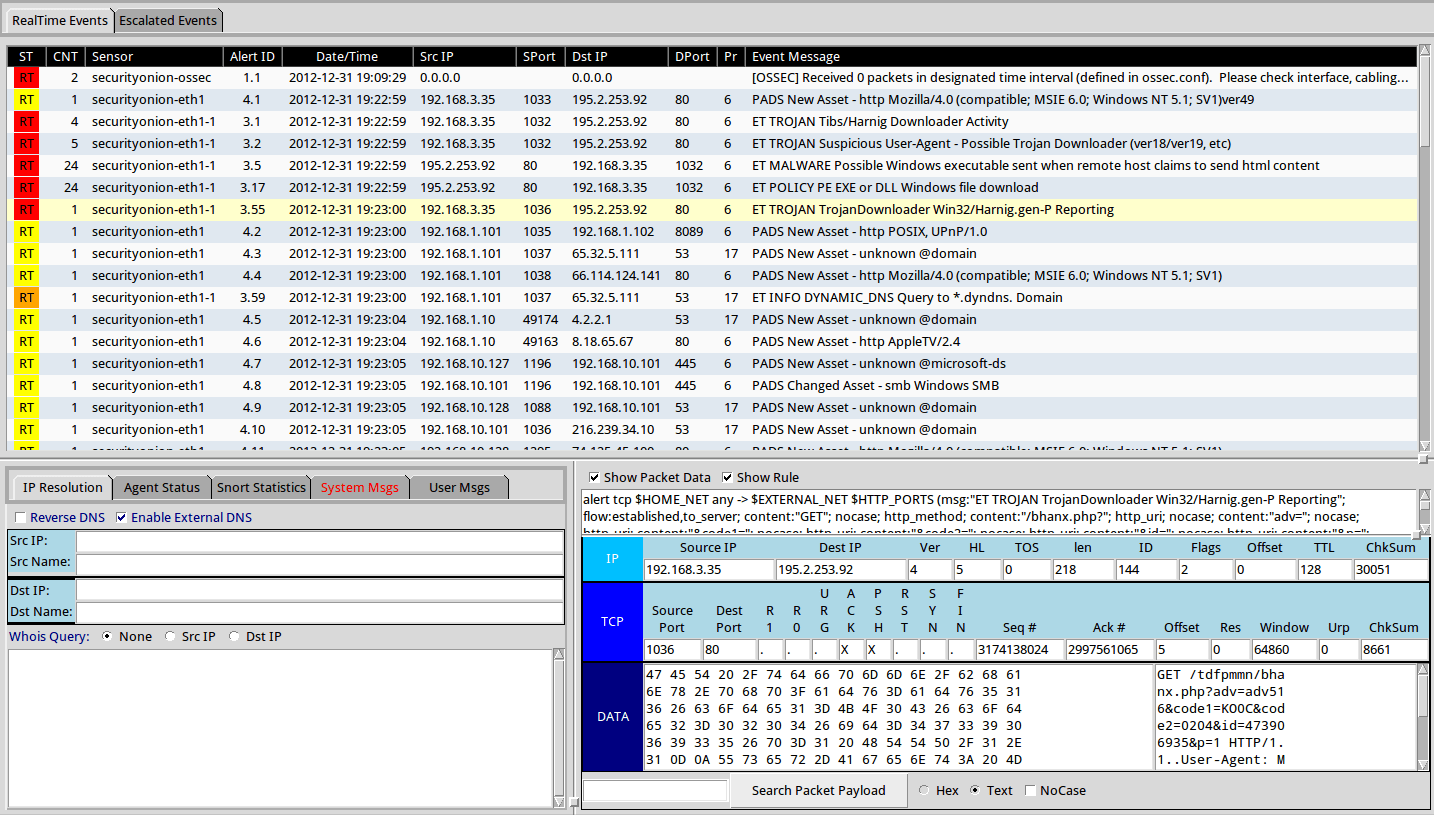
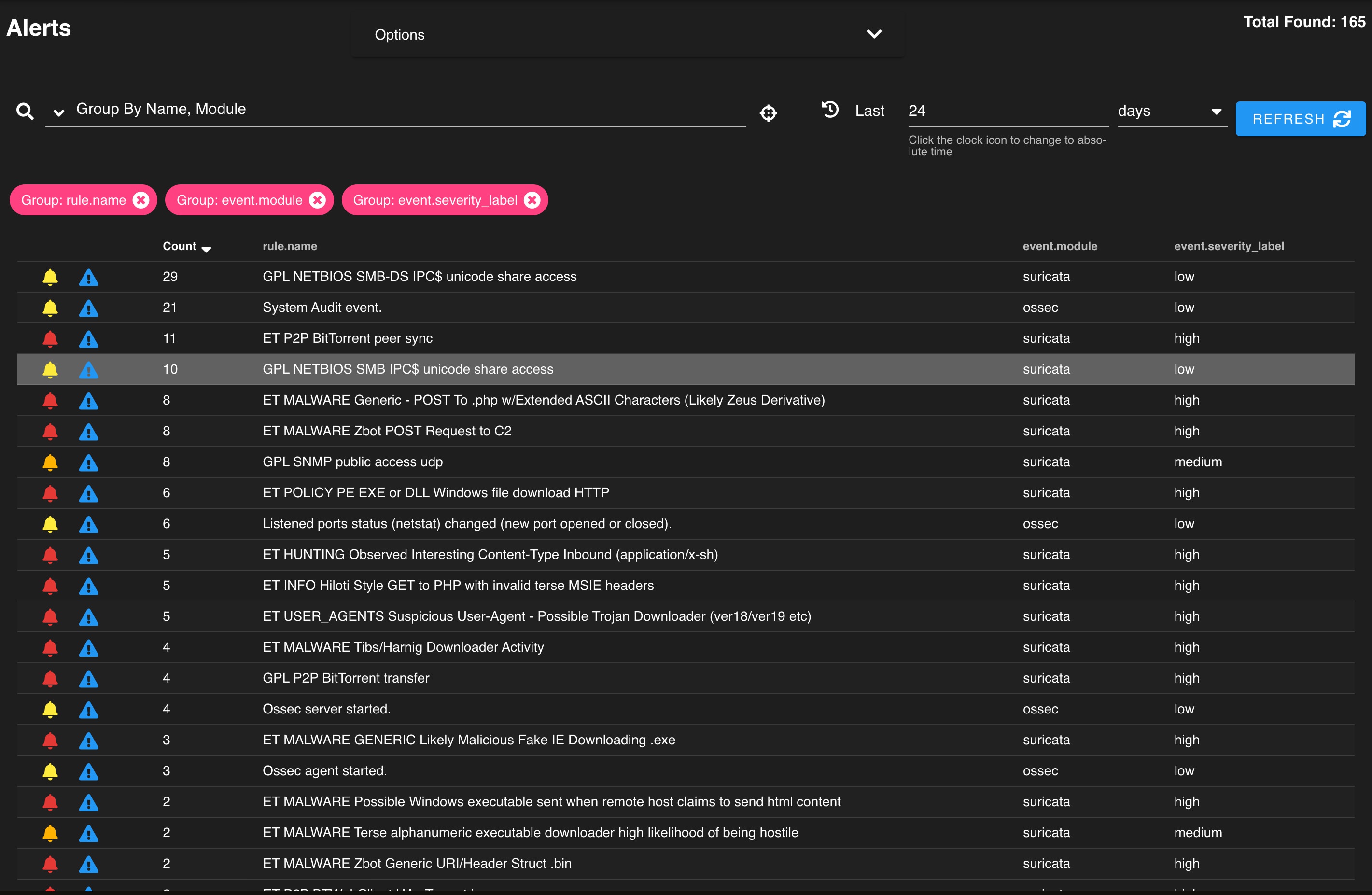
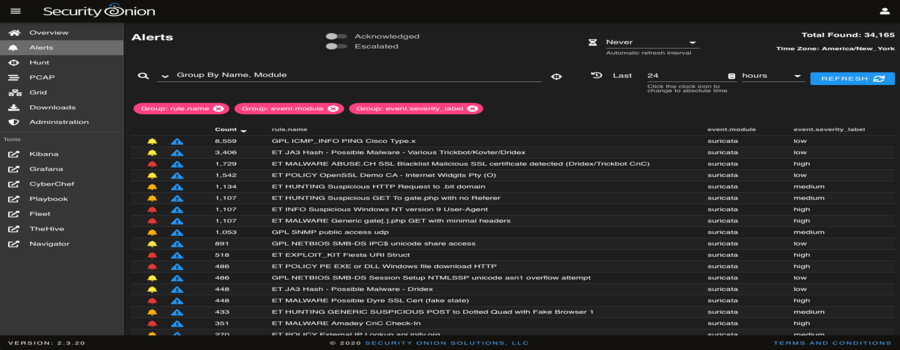
Sysmon & Security Onion, Part 2: Rise of Intelligence-Driven Computer Network Defense – Defensive Depth